Upcoming Computing Technology: SAS 3.0
Continuing our Upcoming Computing Technology series, courtesy of Supermicro NZ, today we’re touching on SAS 3.0 – the next generation in server-grade storage connectors.
More →
Roger Smith Hardware, Server drive, SAS, SCSI, server, storage 0 Comments
Continuing our Upcoming Computing Technology series, courtesy of Supermicro NZ, today we’re touching on SAS 3.0 – the next generation in server-grade storage connectors.
More →
Roger Smith Hardware, Server ddr4, sdram, server, supermicro, technology 0 Comments
 In a recent newsletter, Supermicro NZ touched upon a number of up and coming technology developments that they will be soon to adopt, allowing for greater speed and performance from their servers and desktops. This is exciting for us, since Supermicro is the brand of server we prefer, and often recommend to our customers. More →
In a recent newsletter, Supermicro NZ touched upon a number of up and coming technology developments that they will be soon to adopt, allowing for greater speed and performance from their servers and desktops. This is exciting for us, since Supermicro is the brand of server we prefer, and often recommend to our customers. More →

Roger Smith Linux, Software splash screen, Ubuntu, xmind 0 Comments
 If you have used the Ubuntu version of XMind lately, you may have encountered an annoying bug; While the program itself works, the splash screen hangs in the background and is unable to be closed. Thankfully, there’s a simple workaround. All you have to do is modify the ini file so that the program gets passed the ‘nosplash’ argument on startup, preventing the splash screen from opening in the first place.
If you have used the Ubuntu version of XMind lately, you may have encountered an annoying bug; While the program itself works, the splash screen hangs in the background and is unable to be closed. Thankfully, there’s a simple workaround. All you have to do is modify the ini file so that the program gets passed the ‘nosplash’ argument on startup, preventing the splash screen from opening in the first place.
In order to make the change, enter the following into your terminal:
sudo sed -i '1i-nosplash' /usr/local/xmind/XMind.ini
Hooray! No more annoying splash screen. Credit for the solution goes to user ac:
https://xmind.desk.com/customer/portal/questions/5667621-xmind-startup-bug-in-ubuntu-13-4
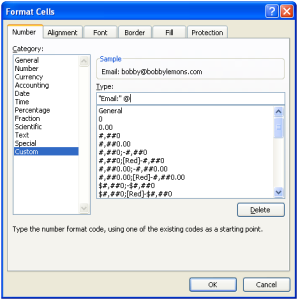
Roger Smith Excel, Microsoft, Office, Software, Spreadsheet Custom formatting, Date, Excel, Gnumeric, LibreOffice, Number, Text, time 2 Comments
Custom formatting is one of those skills that doesn’t take much effort to master, but can really add to the professional appearance of your spreadsheet. With it you can manipulate the format of text and numbers to suit, whether it is the way a date is presented or what colour text will be when a cell contains a negative number. Custom formatting is much the same in any spreadsheet application, whether that is Excel, LibreOffice Calc, or Gnumeric (to name but a few, though for the purposes of this post we’ll be focusing on Excel), and works by using a series of symbols to represent elements like hours, decimal places, and text. By learning these symbols you can create many different formatting variations.
To bring up the custom formatting prompt, highlight the cell you wish to format and press CTRL+1. Select the Custom category and enter your format code into the field below ‘Type:’.
Below are some of the symbols used and examples of things that can be done with custom formatting.
Symbols:
| h | m | s | d | m | y |
| hour | minute | second | day | month | year |
Examples:
| d-m-y | 8-11-12 |
| dd/mm/yy | 08-11-12 |
| ddd mmm yyyy | Thu Nov 2012 |
| dddd mmmm yyyy | Thursday November 2012 |
| dd mmmmm yy | 08 N 12 |
| h m s | 11 45 12 |
| hh:mm:ss | 11:45:12 |
| m/ss | 45/12 |
Notice something in the tables above? The same letter, ‘m’, is used for both month and minute, so how is the spreadsheet able to differentiate between the two? By default, the letter m is treated as month, but preceding it with ‘h’ or following it with ‘s’ tells the spreadsheet to treat the value as a time and adjust the figure for m accordingly.
Symbols:
| #,## | inserts a thousands symbol when the value is greater than 999 |
| 0 | acts as a placeholder for any digits entered |
| 0.0 | Similar to the above, but dictates the number of decimal points |
| ? | A placeholder like 0, but adds a space around insignificant digits so that decimals points line up between values |
| E+0 | Used to show the value in exponent form. |
Examples:
| 000-000-0000 | 031-865-9034 |
| 0.0 | 24.7 |
| #,##0.00 | 3,294.67 |
| 0.0? | 2.9 and 2.94 will line up when stacked vertically |
| 0.00E+0 | 2.45E+5 |
Symbols:
| “” | Used to fix text in a cell |
| @ | Section for text value |
| * | Used to repeat a symbol across the width of a cell. Placed before the symbol to be repeated |
| _ | Used to create a space the width of one character |
Examples:
| 0 ” km” | 74 km |
| @_*> | To the batmobile! >>>>> |
Symbols:
| [Blue], [Black], [Red], etc | Uses the generic colour selected (limited colours) |
| [Color10], [Color15], [Color17], etc | Uses the corresponding colour from the built-in colour palette |
Examples:
| [Blue] | I went to the store today |
| [Color53]#,##0.00 | 4283.97 |
You can find an excellent breakdown of the colour palette here: http://dmcritchie.mvps.org/excel/colors.htm
Another custom formatting feature is to change how the contents of a cell are displayed depending on what value the cell contains. Semi-colons divide this type of formatting into four divisions:
| if value positive; if value negative; if value zero; if value text | Determines how a cell is formatted, depending on the value it contains |
You do not necessarily need to specify anything for the zero and text divisions.
Example:
| $#,##0.00 ” Profit”;$#,##0.00 ” Loss”;”Break Even” | ‘$1,357.23 Profit’ or ‘$3,257.10 Loss’ or ‘Break Even’ |
Like the above, you can also specify the exact conditions under which cell formatting will change:
| [condition] action; [condition] action; | Performs an action depending on the condition given.Works like an if statement |
Notice that the conditions must be typed in using square brackets, so as not to be confused with the positive and negative number formatting shown above. You should end up with something like this:
| [<2000][Red]; [>2000][Color10]; | 1500 or 2500 or 2000 |
That covers many of the options, but if you would like to find out more about custom formatting in Excel you can visit the following help page on the Microsoft website: http://office.microsoft.com/en-gb/excel-help/create-or-delete-a-custom-number-format-HP005199500.aspx.
With a little practice you will be a formatting master in no time!
Roger Smith Microsoft, Security, Software, Windows prompt, Security, unblock, warning, Windows 0 Comments
When opening a file or running a file in Windows, you will often be greeted with a security warning prompt which mentions that the contents of the file could potentially harm your computer. This could be because the file was downloaded from the internet; it may not be properly signed by the developer; or an application of an unknown type is being run (it even displays this warning for software published by Microsoft!)
While this is a nice reminder to have for files from unfamiliar sources, it can be rather irritating for files from developers that you know and trust. Luckily, disabling this warning for individual files is a very simple process:
The next time you open the file, the security warning should no longer appear. A word of warning though – even if the software is from a trusted source, it is still recommended that you have adequate protections in place, such as anti-virus, to make sure that an infected file cannot harm you computer.
Roger Smith Business, Efficiency, Excel, Financial, Software, Spreadsheet Excel, function, investment, net present value, npv 0 Comments
Note: In an earlier version of this post, I had mistakenly used the purchase figure as the first value after rate. I have since been shown that the first value after rate is assumed to be the cashflow in period one, and have since made the correction.
The NPV function is a useful way of calculating the Net Present Value of an investment, and is used to compare the worth of several potential future investments over a set number of equal time periods. Any future expected cash flows are discounted in such a way that the value of money in each period is considered equal (i.e. a dollar next year is worth just as much as a dollar today). If the NPV is a positive figure, the investor is set to receive a positive return.
=period_0+NPV(rate, period_1, period_2, …)
The NPV function consists of two main arguments (or inputs), which are ‘rate’ and ‘value’. Rate represents the expected discount rate of an investment, and is entered as a decimal (i.e. 4% would be entered as 0.04). Value represents the cash flows that are present in each period of the investment, and a new value is entered for each cash flow that occurs (the first cash flow would be entered as value1, second as value2, etc). Cash outflows are entered as negative numbers and cash inflows are entered as positive numbers. The formula assumes that all of the cash flows take place at the end of the period.
As an example, let’s say that you purchase a machine that makes fluoro legwarmers (because, let’s face it, everyone loves the 80s and legwarmers are always stylish). You purchase the machine for $50,000 at the beginning of year one (which in this case would mean the end of Year 0), and determine that the discount rate for all future cash flows is 8%. For the first three years, the machine is expected to return you $12,000, $10,000, and $13,000 respectively.
To calculate the NPV, the above information would be entered into Excel like so:
This returns you a figure of -$19,995.68, which means that at the end of the third year the investment is generating a loss. This is because the initial cost of the machine has still not been recouped by the cash inflows that it has generated. From here, the investor can decide whether their investment period is reasonable (maybe 5 years is more appropriate?), or whether the idea is simply unprofitable.
Roger Smith Internet, Security, Social bill, gcsb, government, Privacy, Security 0 Comments
Gravity Computing has taken a strong stand against the controversial GCSB bill. Eric (our managing director) has taken to social media in earnest over the last few weeks; Roger has turned up in person at protests and rallies; and Ross took an evening a couple weeks ago to travel to Auckland with the team to represent our company and our clients against this bill.
Last night Eric and Roger attended an urgent “Stop the GCSB Bill” public meeting at the Auckland Town Hall to show support for the movement. The turnout was nothing short of amazing with over 1600 people attending in person, and a whopping 140,000 viewing the coverage online.

Eric and Seeby Woodhouse posing for a photo outside of the Auckland Town Hall after the recent “Stop the GCSB Bill” meeting (Apologies for photo quality).
A star panel of speakers were assembled, varied in their backgrounds and fields of expertise: two of New Zealand’s most illustrious investigative journalists; internet entrepreneur powerhouses Kim Dotcom and Seeby Woodhouse; legal experts; human rights advocates, and leaders of almost all opposition parties. Each took a different approach to commenting on the bill and the damage it could cause (from silencing ISPs for fear of prosecution, the chilling effects of a surveillance state, to covering up unethical actions of the military, to exposing the information of beneficiaries), and all emphasising the same point:
This bill is bad news for New Zealand and will strike a huge blow for human rights if it is to come into force.
On a more positive note, there were some familiar faces lingering outside the hall afterwards. Eric (@RhyvenNZ) met fellow Twitter user @endarken in person for the first time, with both of them being active anti-GCSB campaigners on Twitter. Eric got a few photos with some of the speakers, and we even chatted with Seeby Woodhouse for quite a while on some technical aspects of the GCSB and TICS bills.
If you would like to watch the meeting in it’s entirety, take a look at the video embedded below.

Roger Smith Internet, Linux, Security, Software cloud, Privacy, remmina, Security, shared data, spideroak, storage, symbolic link, Ubuntu 0 Comments
Given that Gravity Computing is such a widely-located company, working with sensitive data, it’s important that we have a platform in place that allows us to share resources between each other while keeping them secure. We’ve been using SpiderOak – a cloud-based service similar to Dropbox – which is strongly focused on privacy and security. 
One of those resources we share is the remote connection details for some of our clients. In Ubuntu we use a popular remote connection client named Remmina, which is well regarded for its ease of use and stability. We could each enter the remote connection details into Remmina ourselves, but that would take up unnecessary time and create a time lag if one person is waiting on details from someone else.
A better way of doing it? Create a symbolic link. Remmina stores its remote connection data in a hidden folder in the user’s home directory (i.e. /home/user/.remmina). If we were to store a master copy of the .remmina folder in SpiderOak and then have each desktop link to it, the remote connection details could instantly be accessed and updated from any location.
Even if you’re not all that familiar with the terminal, the process is really very simple. The series of steps below will create a symbolic link between the master .remmina folder and the SpiderOak hive folder. It will delete any Remmina connections that you’ve already saved, so we take a backup of them first.
$ mkdir ~/remminaBackup # Create a folder to contain your old Remmina files $ mv ~/.remmina/* ~/remminaBackup # Move your old Remmina files into your backup folder $ sudo rm -rf ~/.remmina # Remove the existing Remmina directory $ sudo ln -s '~/SpiderOak Hive/Remmina/' ~/.remmina # Create the Symlink $ cp ~/remminaBackup/* ~/.remmina # Copy your old Remmina files into your new Remmina folder
You can delete your remminaBackup folder once you’ve tested your old connections to make sure they still work.
Note that the command is entered in the format “sudo ln -s MASTERLOCATION LINKLOCATION”. Note also that the master location is encased in apostrophes, due to the fact that ‘SpiderOak Hive’ contains a space and would otherwise throw off the command.
Finally, you need to test the Symlink to make sure that it works correctly. The easiest way to do this is to navigate to the .remmina folder in a terminal and check that it contains the required files:
$ cd ~/.remmina # Enter the .remmina directory $ ls # Check the contents of the .remmina folder
You should be greeted with a folder that contains .remmina files, and is identical to your master Remmina folder. If this is not the case, make sure that you have entered in both locations correctly, and that any file path longer than the current folder begins with a backslash.
And voila! You now have a secure repository allowing all your PCs and Servers to be shared within your team.
Roger Smith Passwords, Security, Software algorithm, Hash, iterate, key stretching, password, salt 0 Comments
One thing that you’ll find with most hash functions is that they are designed for speed. With that in mind, you would think that a hash that is both secure and fast would be good, right?
NOPE.
Computers are normally all about speed and efficiency – except for with passwords. When creating password hashing algorithms, you should aim to make them as slow as possible (within reason).
Take a second and read that again, because it’s actually a bit weird. There’s a really good reason to aim for a slow hashing algorithm, and it all comes back to the goal of making Rainbow Tables ineffective or uneconomical. More →
Roger Smith Excel, Software, VBA compare, Excel, queryperformancecounter, thousandth, time, timer, VBA 0 Comments
When debugging code in VBA, it can sometimes be useful to measure how long a particular action takes to complete. In-built functions such as Timer can return you a time as accurate as 1/64th of a second, but what if you need to compare times with a greater degree of accuracy? More →
